Gerard Vince Lillo
About Me
My career is built on one simple principle: if there's something I don't know, I will learn it. This attitude is my core driver, especially in a field like cybersecurity that evolves by the minute. I'm deeply fascinated by the intricate puzzle of defending digital systems. This fascination drives me to translate theory into practice, whether that means automating defensive workflows, hunting for threats in logs, or conducting penetration tests to find weaknesses.
I thrive on turning unknowns into strengths. Whether it's mastering a new security framework, dissecting an unfamiliar threat, or architecting a more resilient cloud environment, my process is the same: learn the things I don't know and continuously improve. For me, challenges aren't obstacles; they're opportunities to expand my skill set and build more intelligent defenses."
Core Skills
My Arsenal
Development & Automation
Python
- Automation Scripts
- Vulnerability Parsing
- Log Parsers
- API Integration
AWS
- IAM (Identity & Access)
- VPC & Security Groups
- EC2 & S3
- Lambda & SQS
Linux CLI
- System Admin
- Bash Scripting
- Tool Installation
- VM Management
Jira
- Workflow Design
- Board Creation
- CI/CD Integration
- Ticket Automation
Commvault
- AWS Inventory
- License Calculation
- Storage Pricing
- Backup Solutions
Vulnerability & Penetration Testing
Prowler
- CLI Setup
- AWS Account Scanning
- Report Generation
- CSPM
Plerion
- AWS Account Scanning
- Vuln Analysis
- Remediation Research
- Cloud Security
Nmap
- Network Scanning
- Service Discovery
- OS Fingerprinting
- Vuln Assessment
Metasploit
- Exploit Development
- Payload Crafting
- Post-Exploitation
- Penetration Testing
OWASP ZAP
- API Fuzz Testing
- Web App Scanning
- Session Analysis
- Vulnerability ID
Security Operations & Defense
Bitdefender
- AD Integration
- Endpoint Deployment
- Relay Configuration
- 400+ Endpoints
CrowdStrike
- Falcon SOAR to Jira
- Server Deployment
- Endpoint Detection
- Threat Intelligence
Splunk
- Alert Triage
- Incident Documentation
- IoC Analysis
- Health Checks
Wazuh
- SIEM Hosting
- Log Management
- Linux CLI Setup
- Secure Access (VPC)
Vision One
- XDR Platform
- Threat Correlation
- Endpoint Telemetry
- Incident Response
Cloud Rewind
- AWS Integration
- EC2 Backup & Restore
- Disaster Recovery
- DR Simulation
VirusTotal
- False Positive Triage
- Domain Reputation
- Vendor Communication
- Threat Analysis
Featured Project
A project built to demonstrate practical, hands-on skills in defensive security engineering and threat detection.
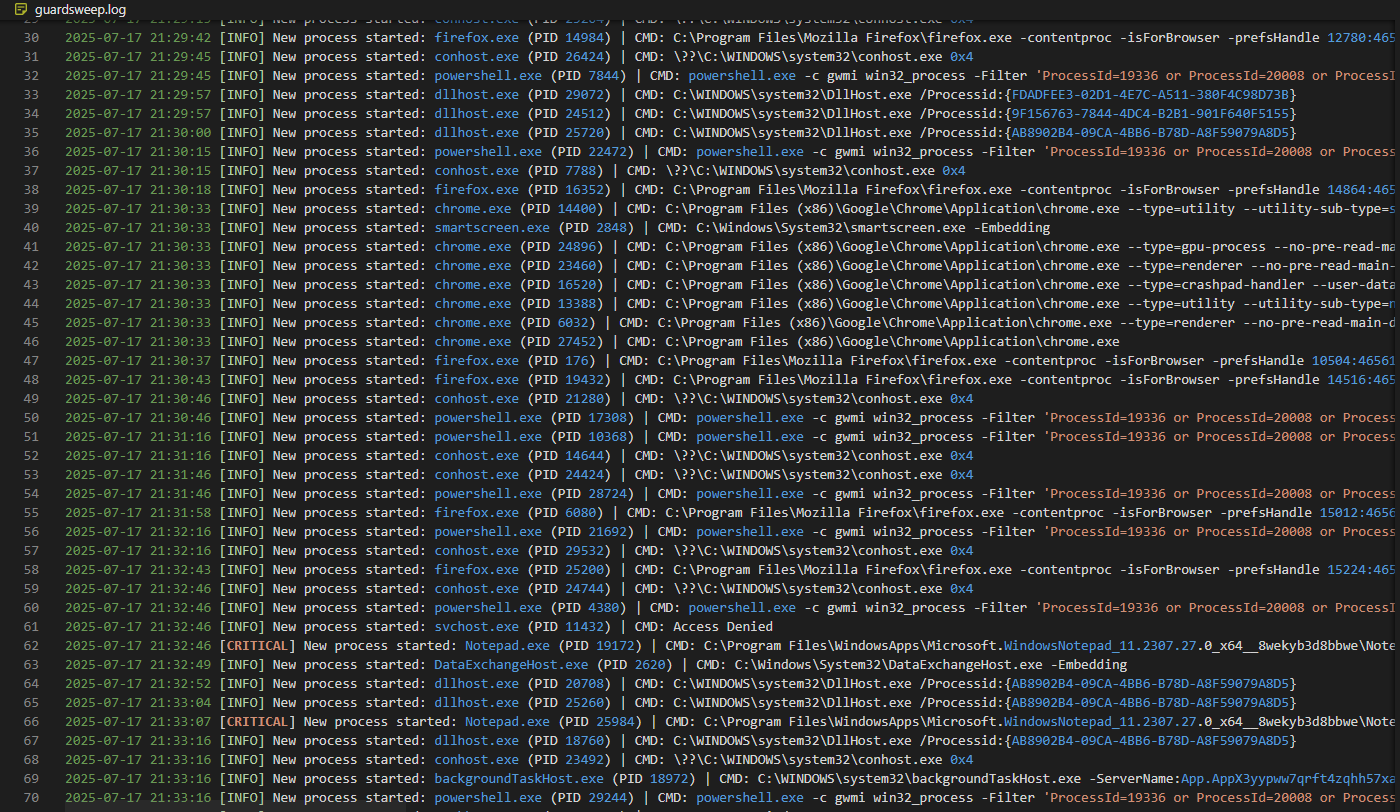
GuardSweep | EDR
A lightweight, cross-platform Endpoint Detection and Response (EDR) tool written in Python. It provides real-time monitoring of system events, including process creation, file system changes, and network connections, to detect and alert on malicious activity.
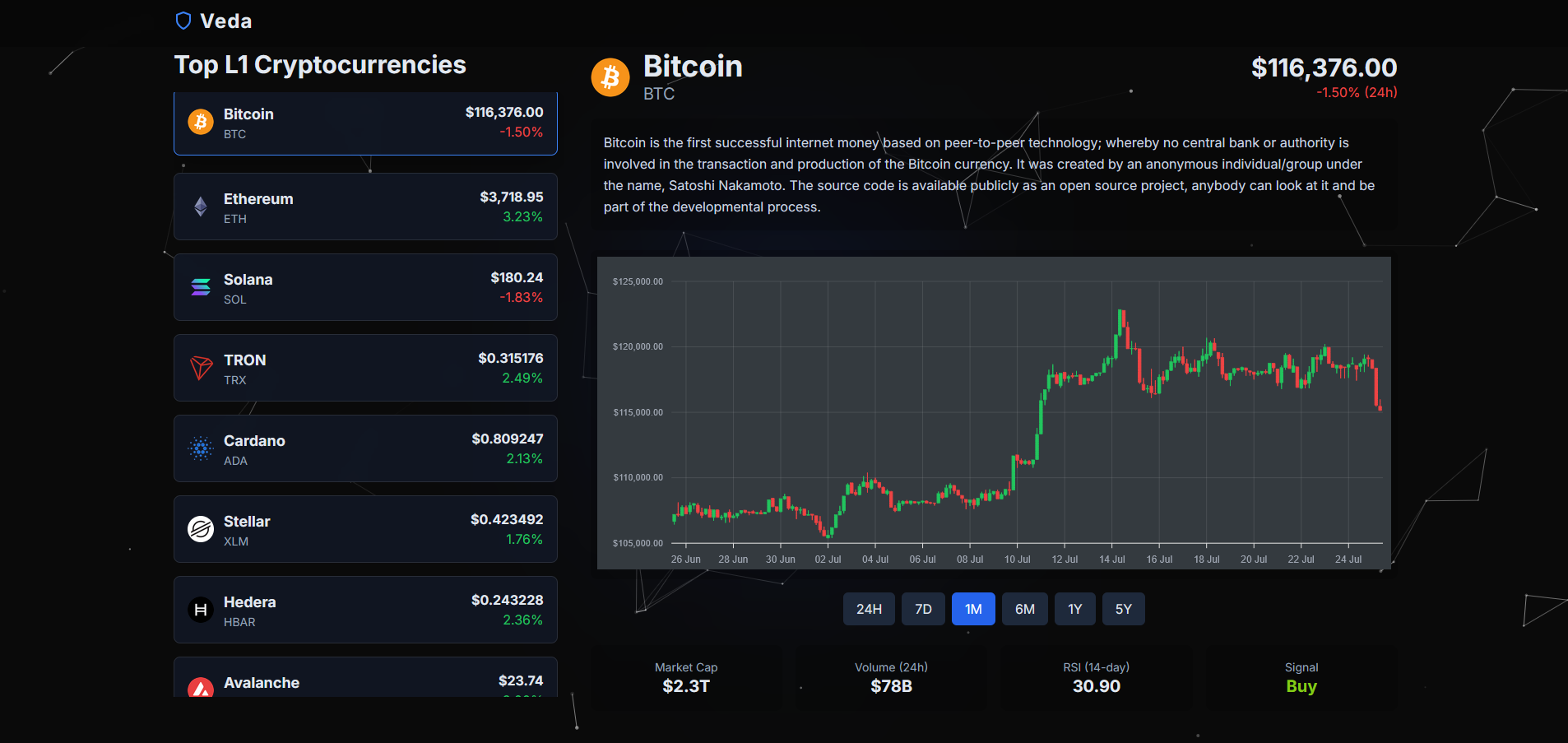
Veda | L1 Crypto Tracker
Veda is a real-time cryptocurrency dashboard that focuses on tracking and analyzing top Layer-1 (L1) blockchain projects. Users can view price charts, compare market cap and volume, and get technical indicator signals like RSI.
Live from GitHub
Fetching latest projects...
Professional Experience
May 2025 - Present
Security Engineer
Cloud Ready Technologies Corp.
- Designed and implemented a CI/CD security pipeline using Bitbucket Pipelines to automate vulnerability scanning with Trivy.
- Developed a Python-based vulnerability parsing script to process Trivy's JSON reports, identifying critical misconfigurations and de-duplicating findings.
- Automated the security workflow by translating the script into a Bitbucket Pipeline that creates Jira tickets for remediation.
- Performed penetration testing for SaaS API endpoints, identifying and reporting critical issues like CORS misconfigurations and token replay vulnerabilities.
- Conducted cloud security posture assessments using Prowler and Plerion to scan AWS accounts, analyze vulnerabilities, and research remediation strategies.
- Configured CrowdStrike Falcon SOAR to automate Jira ticket creation from endpoint detections, improving incident response time.
- Managed endpoint security by deploying Bitdefender BEST to over 400 Windows endpoints using Active Directory integration.
- Led the design of a managed backup service, creating the Scope of Work and performing cost analysis for AWS backup solutions like Commvault.
- Resolved a domain reputation issue by coordinating with VirusTotal and multiple security vendors to clear false positive flags.
July 2024 - April 2025
Security Analyst
Cloud Ready Technologies Corp.
- Monitored and triaged security alerts using Splunk, documenting incidents based on severity and following escalation protocols.
- Analyzed Indicators of Compromise (IoCs) to identify and neutralize threats across multiple client environments.
- Authored weekly health check reports on endpoint malware detection, protection agent status, and policy compliance.
- Provided tailored security recommendations to clients, including system upgrade advisories and mitigation plans.
Jan 2024 - July 2024
Software Engineer
Cloud Ready Technologies Corp.
- Developed Python-based log parsers to automate alert processing and integrate them with Jira for SOC analysts.
- Utilized AWS services like Lambda for serverless execution, CloudWatch for debugging, S3 for storage, and EC2 for hosting Wazuh and Graylog.
- Implemented SQS for message queuing to handle delayed data processing, improving automation and efficiency.
- Configured VPCs and security groups to restrict access and secure Wazuh and Graylog instances.
Certifications
Let's Connect
I'm currently seeking new opportunities. If you have a project in mind or just want to chat, please fill out the form below.